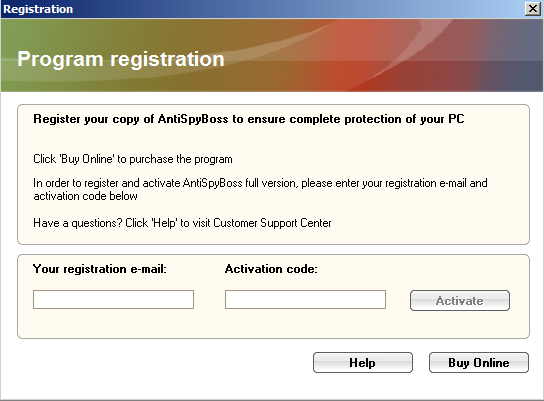
Antispyboss, a well-known relic of the digital past. In classic rogue fashion, Antispyboss users are treated to a parade of counterfeit infections, each more imaginary than the last. AND for a modest registration fee you gain the privilege of parting ways with these virtual specters.
Today, for educational purposes, we’ll craft a keygen for this maleficent artifact and learn a little about how md5 hashing can be used in serial generation.
Virus Total Results
 Virus Total Results for Installer
Virus Total Results for Installer
First Run
After installing, a “scan” is performed. The rogue actually writes random files to random locations and then “detects” said files as “threats”. Yeesh. See below.
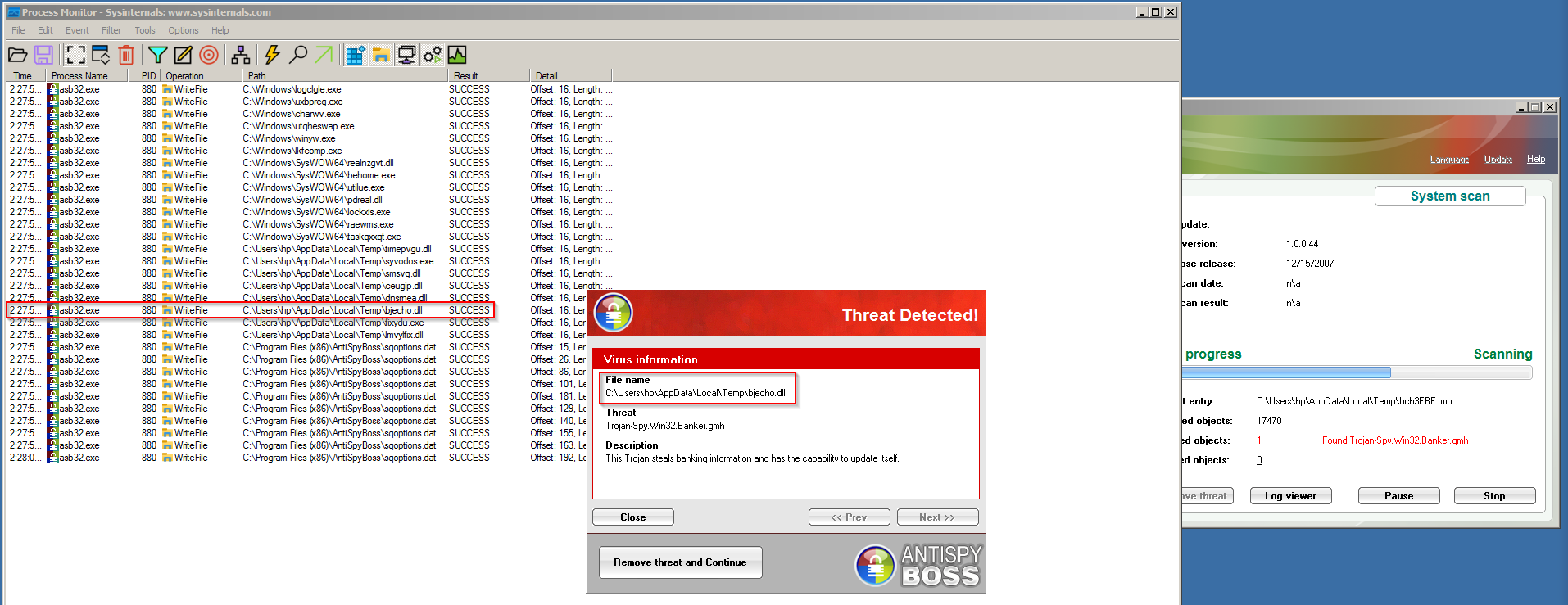 Process Monitor showing AntiSpyBoss writing fake malware to the hard drive
Process Monitor showing AntiSpyBoss writing fake malware to the hard drive
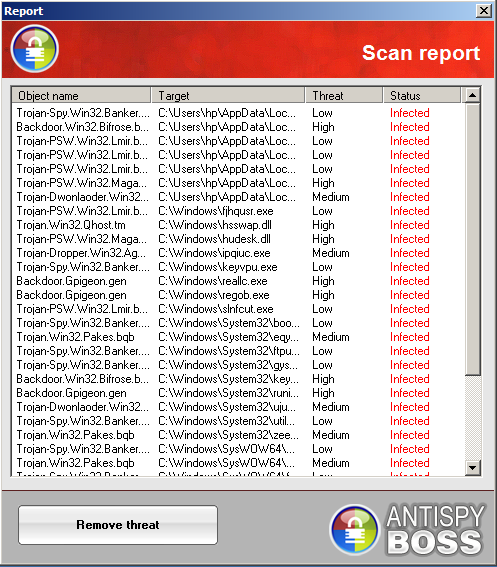 Shows many fake infections on clean VM box
Shows many fake infections on clean VM box
Registration Routine
Once the registration routine is found, we notice an interesting string ‘edinichka’ as well as a jump further down that may jump over successful registration message.
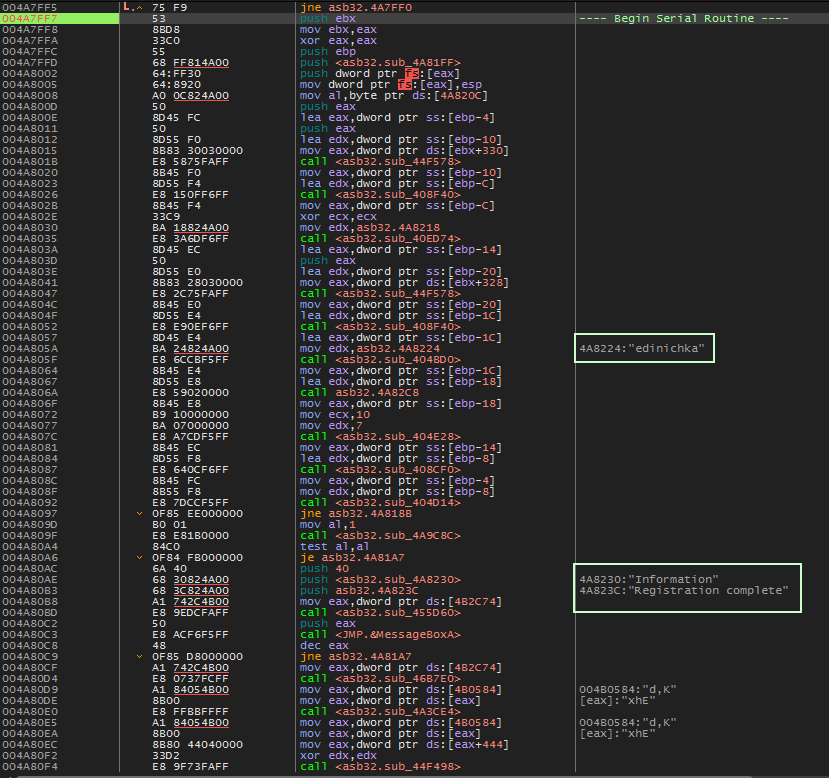 Shows the registration routine
Shows the registration routine
Stepping over each instruction, we eventually see that ‘edinichka’ has been appended to our email address. We will step into the following call (call asb32.4A82C8) to see what is going to happen to this new string.
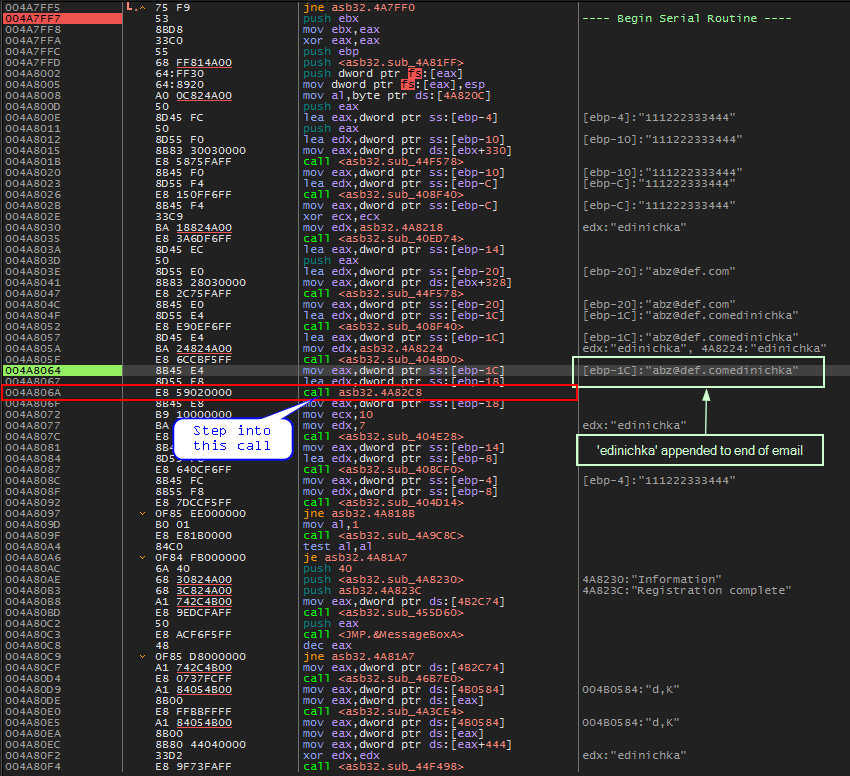 edinichka appended to email address
edinichka appended to email address
Entering the call we see some wincrypt functions. Noteably: CryptCreateHash, CryptHashData and CryptGetHashParam Stepping through, it is obvious to see that our newly formed email string is about to be hashed. The algorithm that will be used is MD5 as noted by the ALG_ID of 0x8003. We can follow in dump, the location where the hash will be placed.
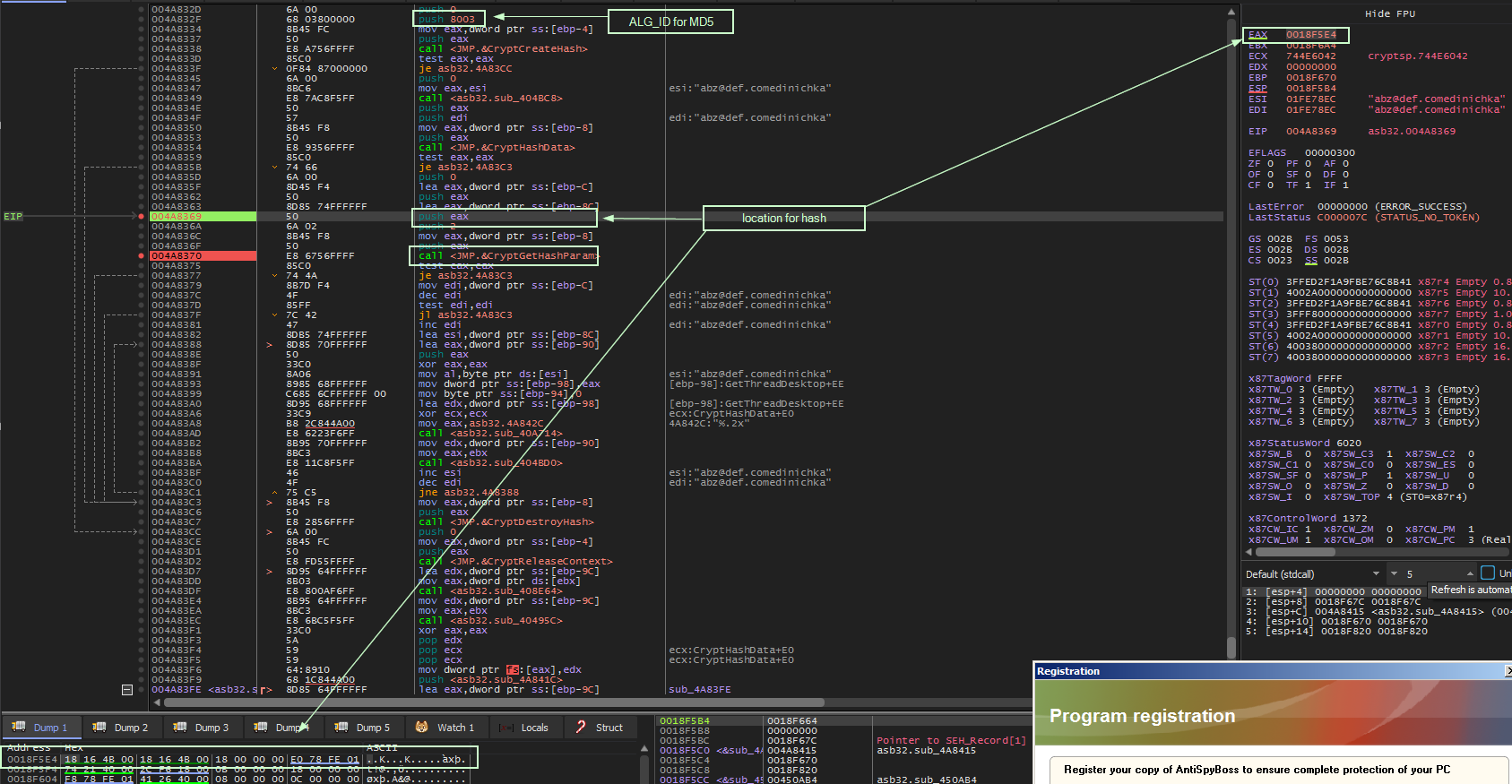 crypt hash functions
crypt hash functions
After CryptGetHashParam is called, we can see the hash has been placed the dump location.
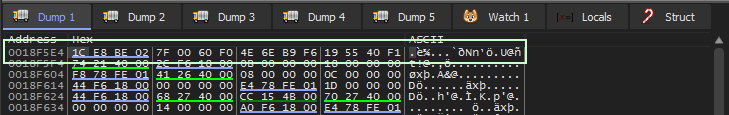 md5 hash of email+edinichka
md5 hash of email+edinichka
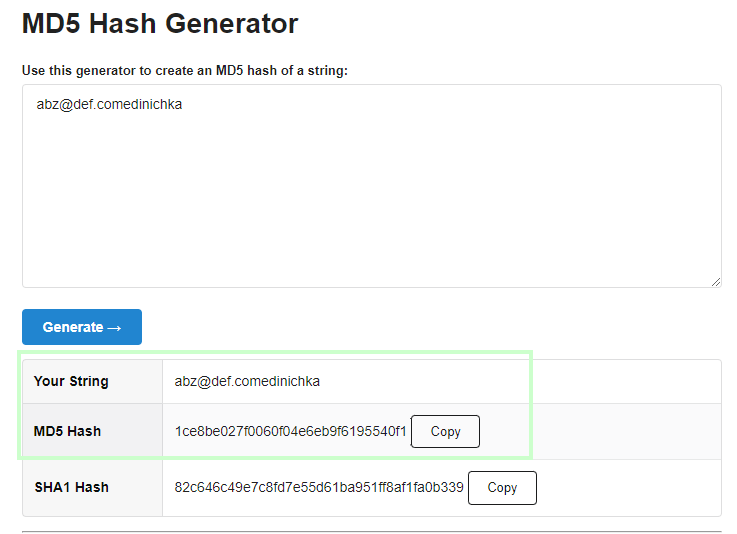
We can check that this is indeed an md5 hash by using an online md5 hash generator with our email: ‘abz@def.comedinichka’
After this, the only thing of interest that seems to occur is our hash being converted to upper-case.
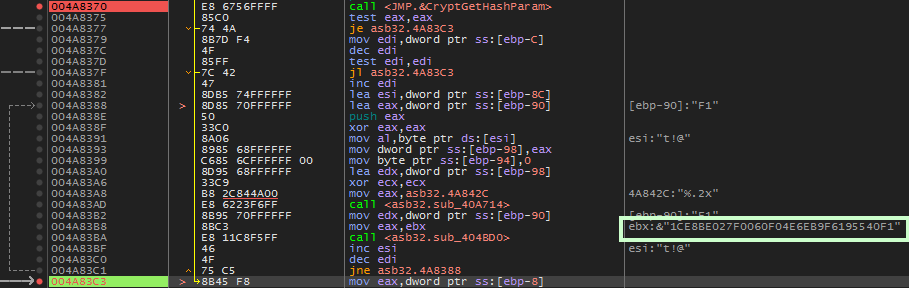 hash to upper-case
hash to upper-case
We are returned to the main registration routine where we can see that it appears our inputed serial will be compared with the md5 hash. However, the first 6 chars and the last 10chars have been removed from our md5 hash.
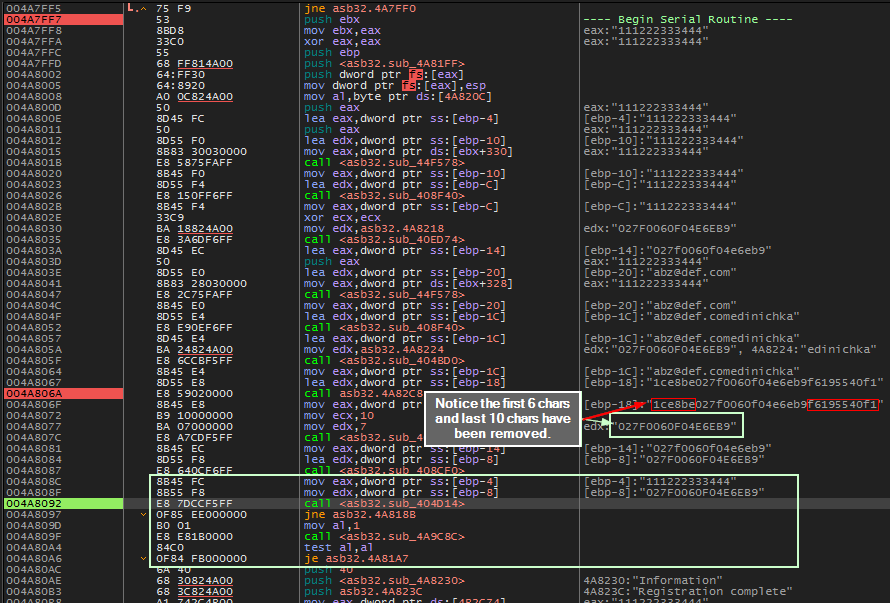 Compare about to occur. First 6 chars and the last 10 chars have been removed from md5
Compare about to occur. First 6 chars and the last 10 chars have been removed from md5
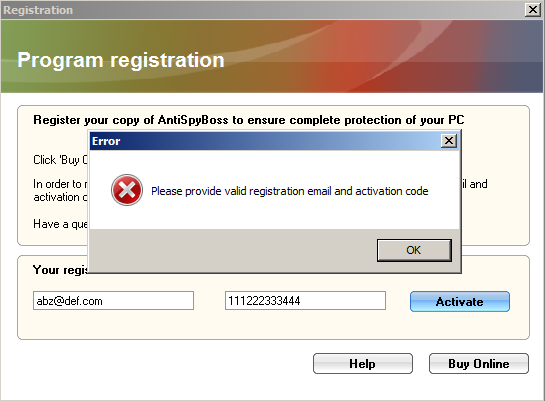
Of course our input serial doesn’t match and we are presented with the error message. Let’s try the md5 hash minus the first 6 chars, last 10 chars and see if it works.
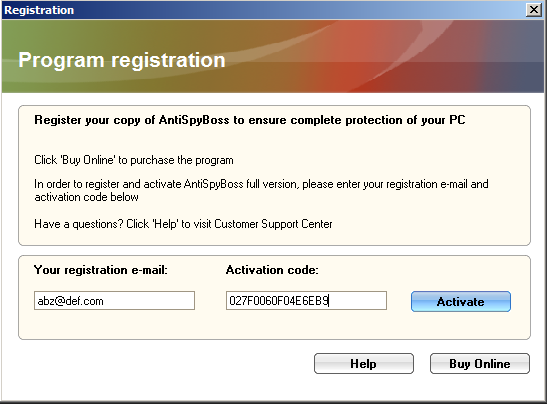 Entering the md5 hash minus first 6 chars
Entering the md5 hash minus first 6 chars
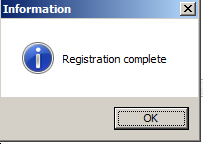
And we are presented with a rather anti-climactic success…
Coding the Keygen
Our task here is pretty simple:
- Get email address
- Append the word ‘edinichka’ to email address
- Get md5 hash of above
- Remove first 6 chars, last 10 chars of md5 hash
- Conquer the world
1
2
3
4
5
6
7
8
9
import hashlib
email = str(input('Enter email: ')) # get email from user
email += 'edinichka' # append 'edinichka''
m = hashlib.md5(email.encode('utf-8')).hexdigest() # md5 hash
m = m[6:22].upper() # take chars from index 6 to 21
print(f'Serial: {m}')