While working on the last ‘Reversing Rogues’ blog post (See it here) I noticed that SpyFighter.exe was packed with UPX.
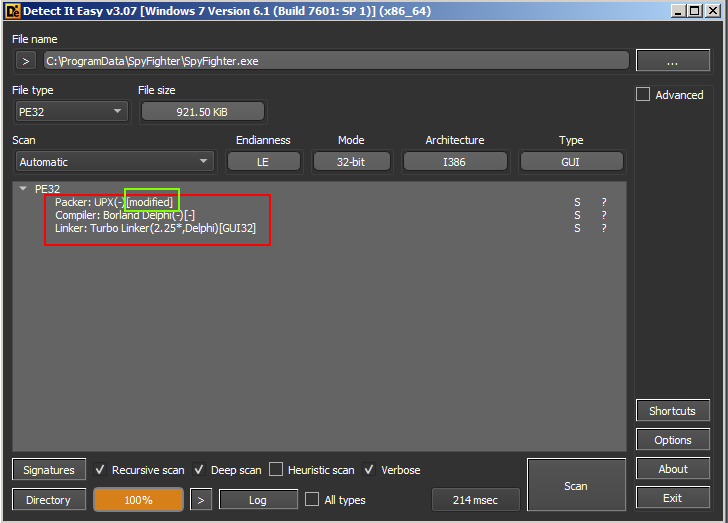
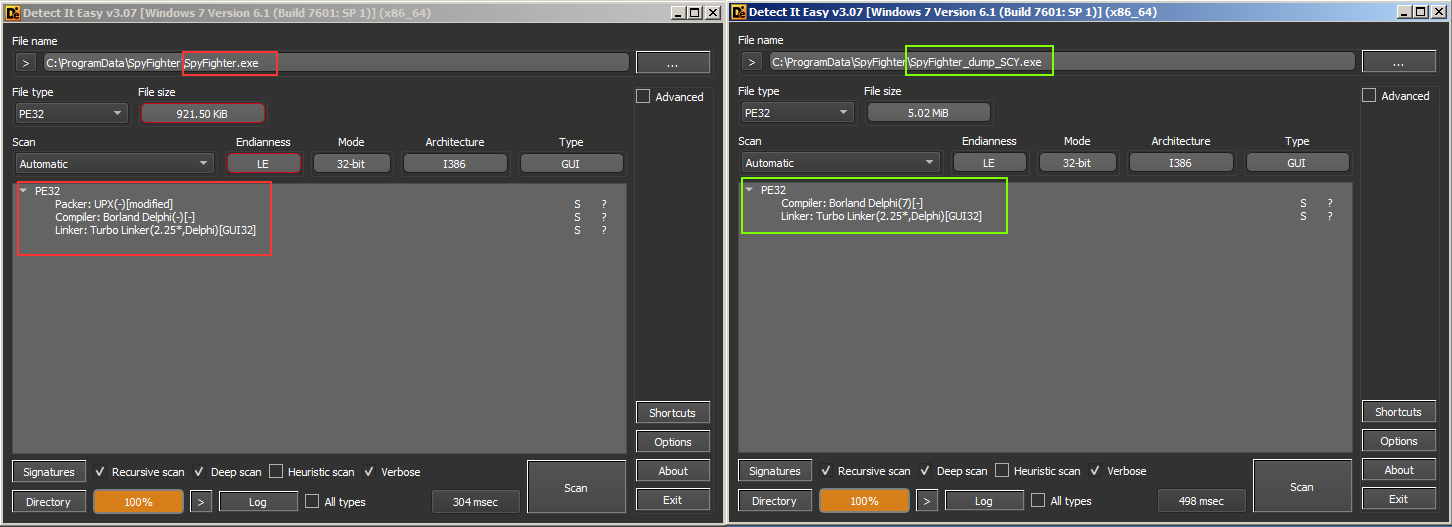
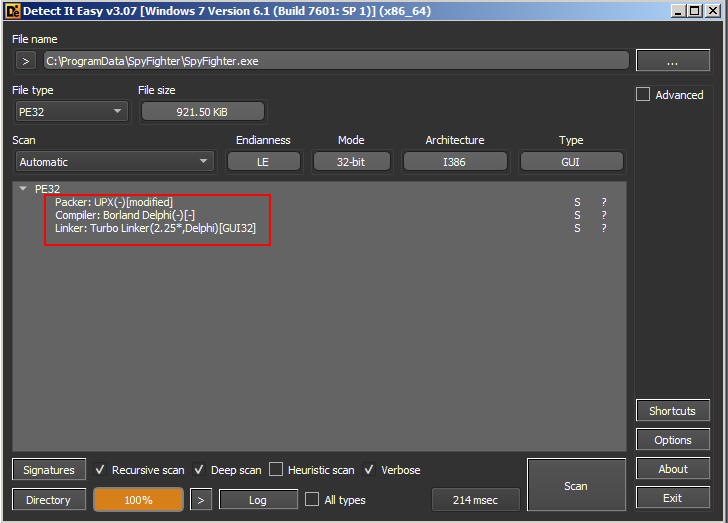 Detect it Easy showing SpyFighter packed with UPX
Detect it Easy showing SpyFighter packed with UPX
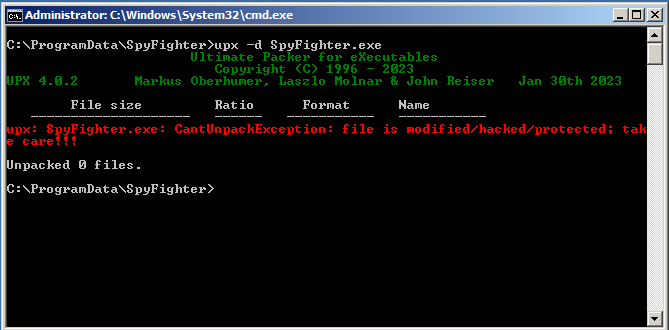
So, I decided perhaps I should unpack it. Easy enough with UPX installed, simply run the command:
upx -d spyfighter.exe
And we should be good. However, I was met with this interesting message:
Unpacking with UPX itself has failed. Let’s dive in.
What is UPX?
UPX, short for Ultimate Packer for eXecutables, stands as a popular open-source executable file compression tool. Often employed in software development to reduce file sizes without compromising functionality.
UPX finds an unexpected application in the world of malware. Malicious actors frequently use UPX to compress and obfuscate malware, aiming to evade detection by security software and complicating analysis by cybersecurity professionals. This tool’s dual nature—valued in legitimate software development and misused in the realm of malware—creates a unique and complex landscape for cybersecurity experts.
What’s wrong?
Why can’t UPX unpack our sample of SpyFighter? Let’s take a look at the ‘Detect it Easy’ results again and we notice the bit highlighted below. Our packed sample has been modified.
Breaking the ability to use the upx -d command is suprisingly easy. Simply changing 1 byte in the packed binary is enough. Perhaps this is what was done with this file. We could take a look at it within a hex editor and perhaps we would get lucky. Maybe we’d find exactly what was modified. However, I decided to forego this and opted to manually unpack the sample.
Why Unpack?
Unpacking malware, despite its inherent risks, is crucial for cybersecurity analysts aiming to understand its behavior, identify its components, and develop effective countermeasures. Unpacking allows for deeper analysis, revealing hidden code, functionalities, and potential vulnerabilities within the malicious software. Understanding the malware’s inner workings aids in creating better detection signatures, improving security software, and developing mitigation strategies to protect against similar threats in the future. While fraught with potential dangers, unpacking malware remains a fundamental step in comprehensively combating and safeguarding against evolving cyber threats.
How to Unpack Manually
Ok with that out of the way let’s look at just how easy it is to unpack UPX manually.
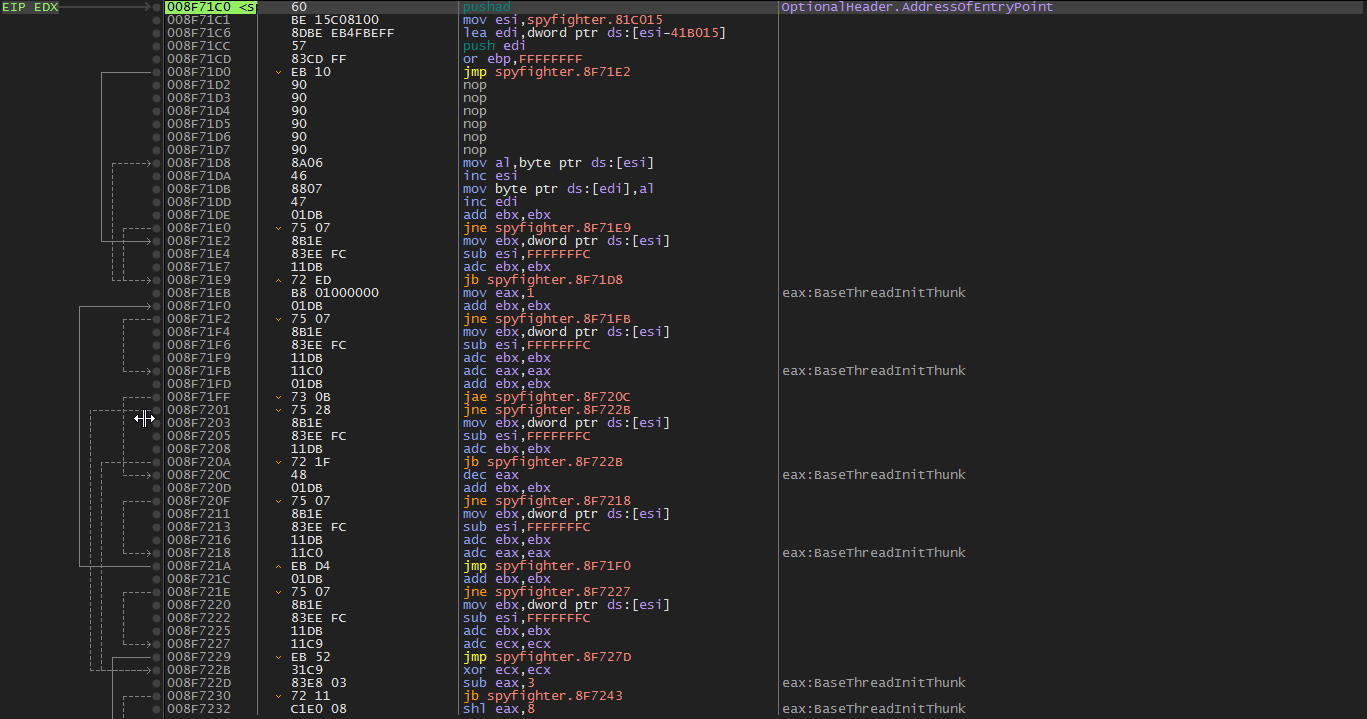
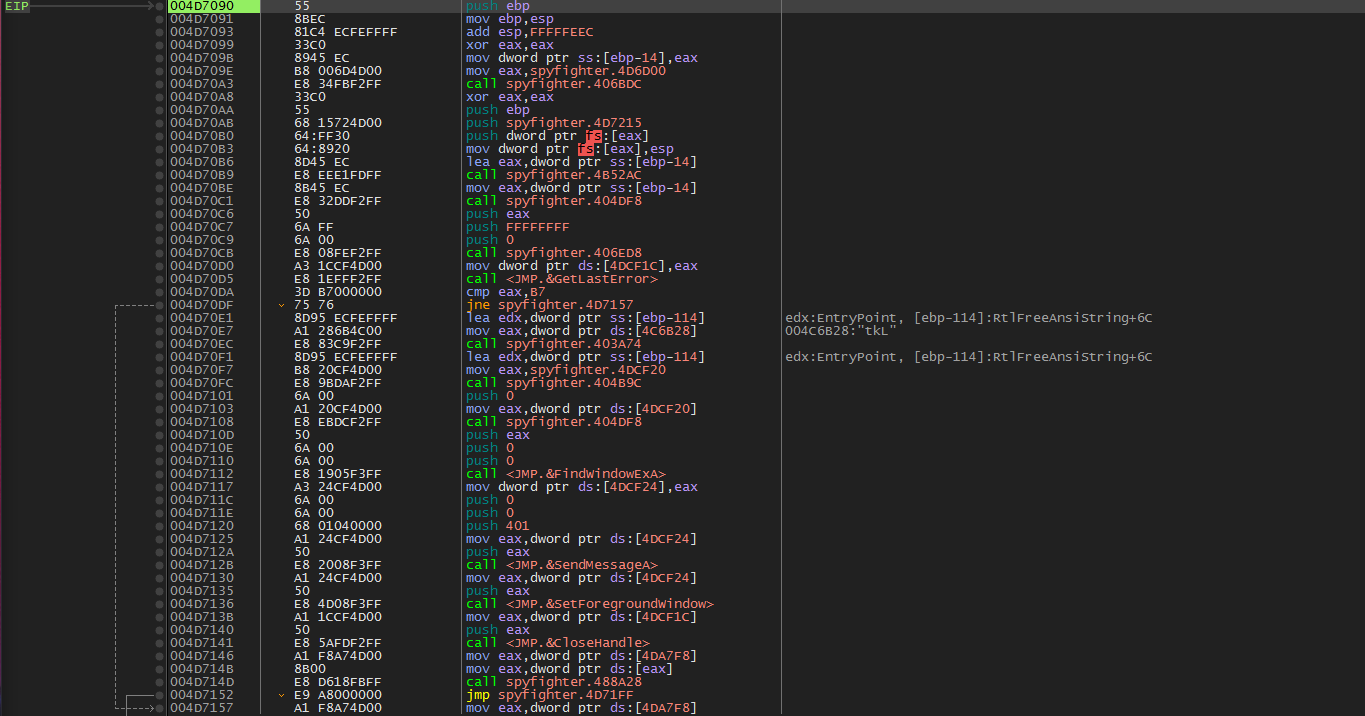
Loading the executable into x64dbg and press the run(f9) key, we immediately break here on the pushad instruction. The classic UPX start. This instruction will push all of the working registers on to the stack where the will stay safe and sound until perhaps the file is unpacked and they are ready to be brought back…
Let’s scroll down until we hit a jne just before a jmp followed by empty space. This is, again, classic UPX style. The final jmp instruction should take us to our OEP.
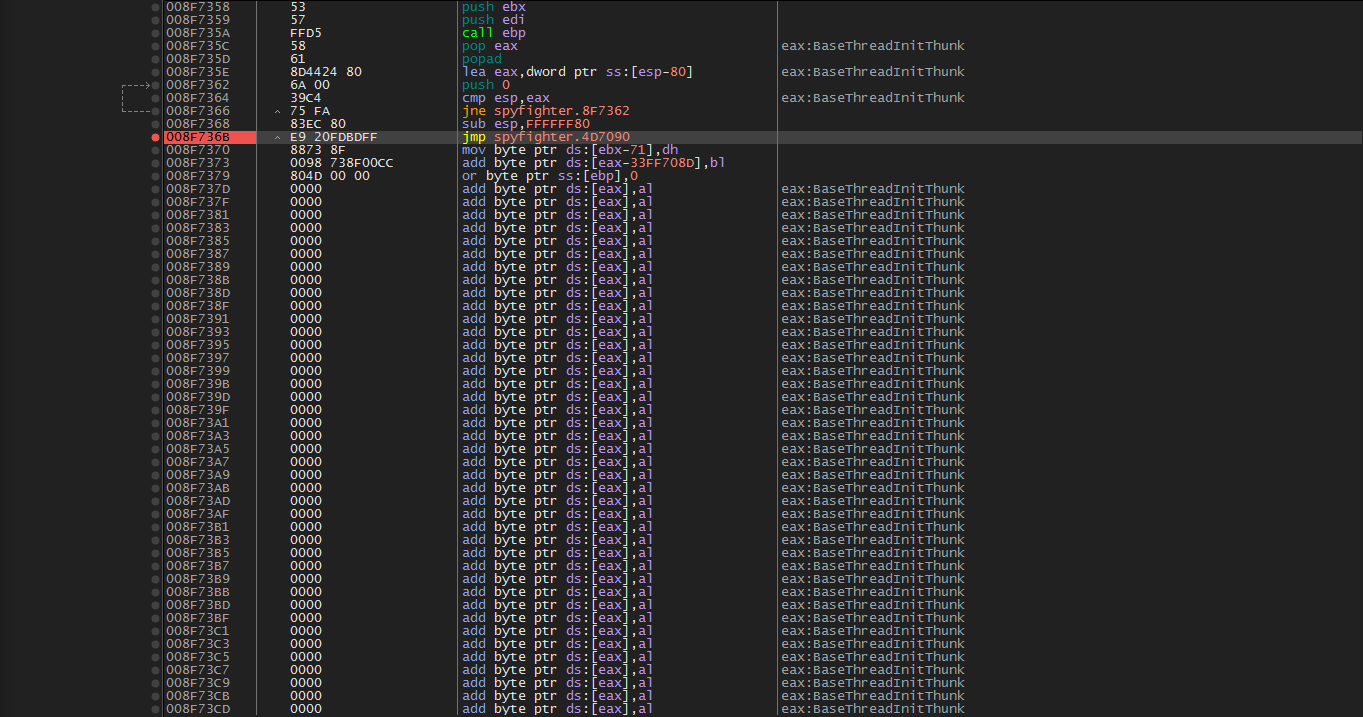
Let’s set a break, and run(f9). We will break then step (f8) once, and end up here. The OEP.
We are now ready to dump the memory. To do that we will make use of the scylla plugin for x64dbg.
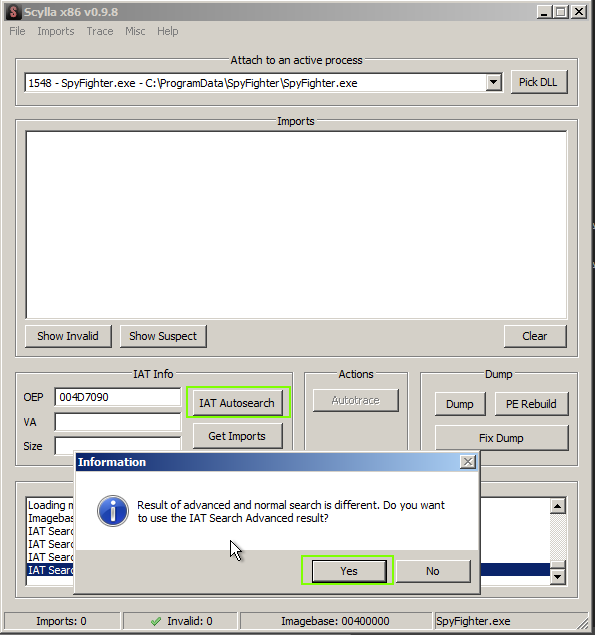
Once Scylla is opened, we are presented with the screen below. We will choose ‘IAT AutoSearch’ and ‘Yes’
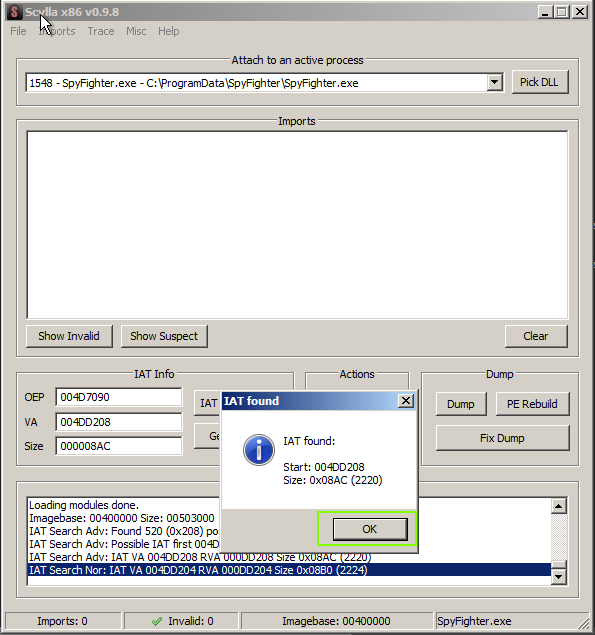
Hopefully, our imports were found and we can click ‘OK’
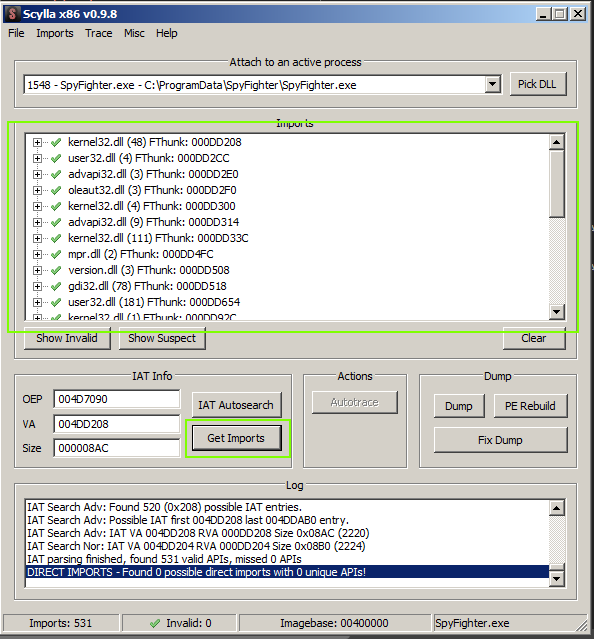
Next, choose ‘Get Imports’ and scroll through them to ensure they are all found (green checks)
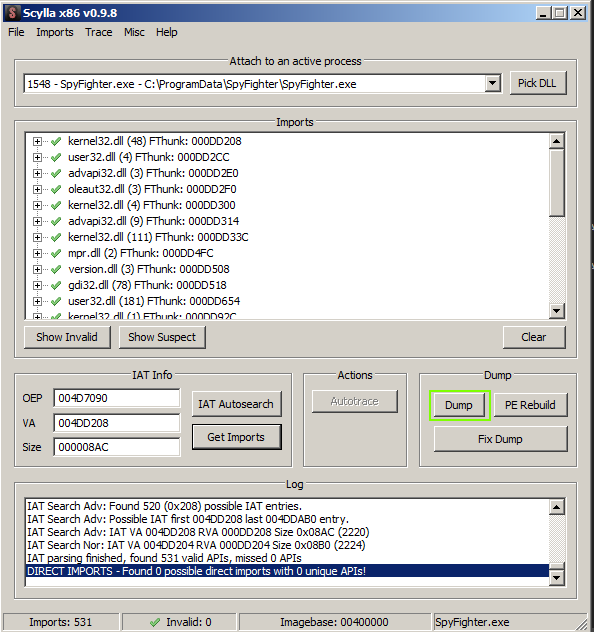
Now, we can dump and save the dump.
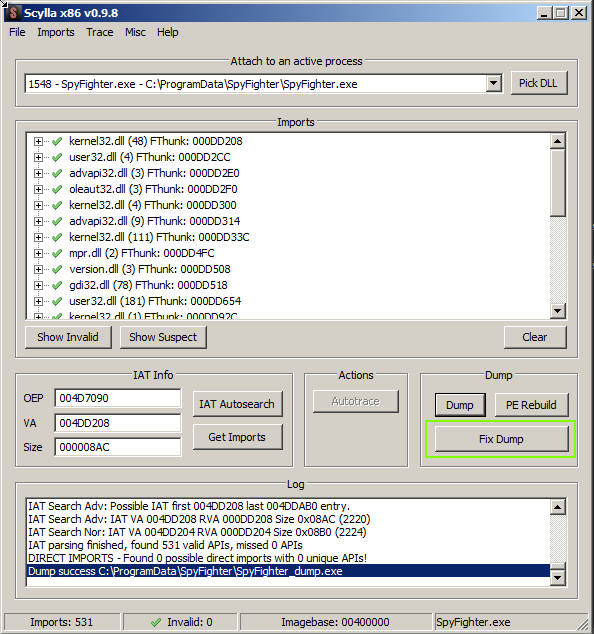
After that, we simply fix the dump by selecting ‘Fix Dump’ and choosing the ‘dump’ exe we saved in the previous step.
We can see that our fixed dump was saved with a trailing ‘SCY’.
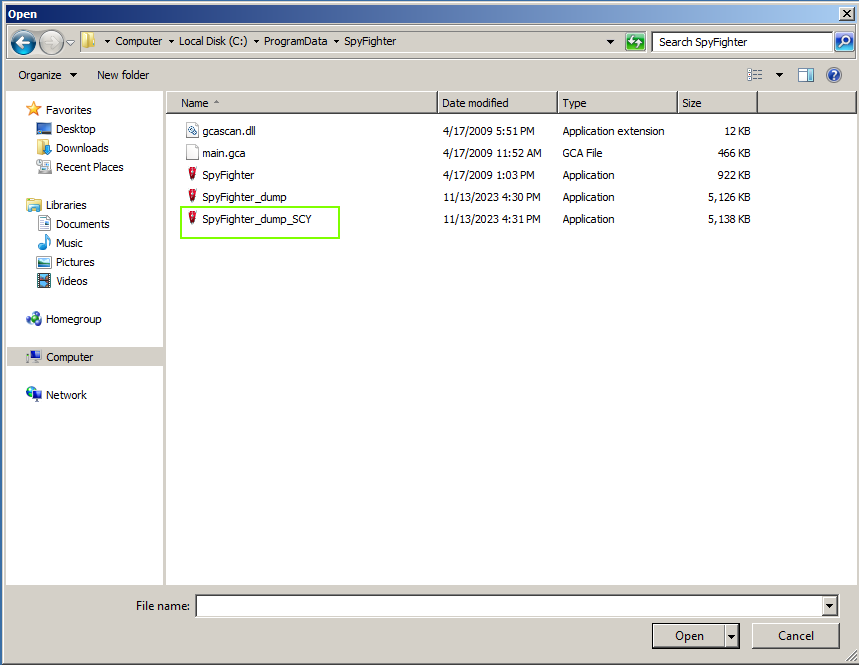
That’s it. We’ve successfully unpacked a UPX compressed executable. Let’s see what DiE says about it.